Complete the following Information Security Technologies assignment
Complete the following Information Security Technologies assignment (100 marks in total).
Exercise 1: Symmetric encryption and decryption
- Go to http://www.math.brown.edu/~jhs/MathCrypto/CipherWheel.pdf and print the wheel or save the file on your computer. (a) Calculate the shift number.
- Go to http://substitution.webmasters.sk/simple-substitution-cipher.php . Check ‘Julius Caesar Cipher’ and enter the shift number you calculated above. Then enter the following plaintext: “This is a very exciting exercise for Information Security Technologies. I like cryptology.” And click on Encode/Decode. (b) What is the ciphertext?
- Now check ‘Simple substitution cipher’. Open another viewing window and go to
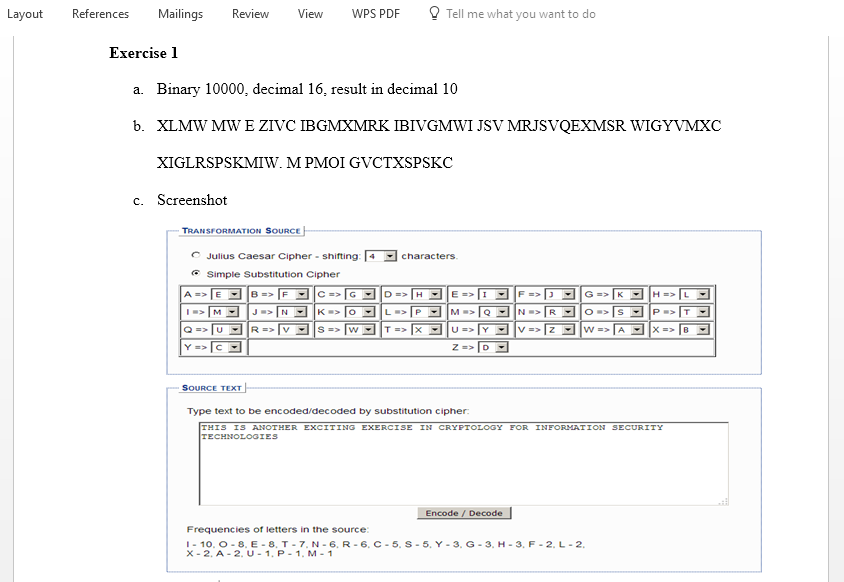
www.cse.ohio-state.edu/~lai/651/2-Classical%20Encryption.ppt . Go to slide 22. Using the information on that slide, enter the substitution scheme into the substitution options you have on the substitution cypher tool. Update the letters in the Transformation Source box. Encode the plaintext: “This is another exciting exercise in cryptology for Information Security Technologies”. (c) What is the ciphertex? Include a screenshot of your substitutions, plaintext and cipher text. - Go to http://rumkin.com/tools/cipher/caesar.php . Copy and paste the following cipher text into the ‘Decode a cipher’ box: VOKBXSXQ KLYED MYWZEDOB CMSOXMO SC PEX KXN BOGKBNSXQ. Start without help and then use Rotate repeatedly. (d) What is the plaintext and (e) what is the key?
- Go to http://ba.net/util/cipher2/cipher.html . Copy and paste: “On this page you can create and solve simple substitution ciphers. In a substitution cipher, each letter of the alphabet is replaced with a different letter” into the ‘Create a cipher: Enter your plain text here’ box. Click on the ‘Substitution Cipher’ button. Copy and paste the ciphered text into ‘Decode a cipher’: enter your enciphered text here’ box. Then using the ‘Command Line’ box and with knowledge of the plaintext, work out the key by individually swapping letters. Make a note of every swap. (f) What is the substitution key table?
- Download the file codes_u1_text.pdf from blackboard (in the same folder of this assignment description). Read the document and go to the last activity at the end of the document. You are provided with a cipher text and some clues as to how to decipher this cipher text using these clues and the frequency table. Try to go as far as you can with the decryption. (g) What is the plaintext?
Exercise 2: Hashing and asymmetric encryption and decryption
- Go to http://sourceforge.net/projects/md5deep/?source=directory and click download md5deep and select Windows binary and download the latest version of the program – or download the Hashdeep files off AUTOnline. Save and store the program on your computer or flash drive to make navigation to them easier, since you will have to run the program using the command prompt. (Never used the Command Prompt before? Check out: http://pcsupport.about.com/od/termsc/p/command-prompt.htm )
- Extract the files. First, create two Word documents, each only containing one line, as follows: Now is the time for all good men to come to the aid of their country. Save the file first in country1.doc and, after adding a full-stop to the end of the line, save the second to country2. doc, both in the same directory as the md5deep.
- Start the command prompt and navigate to the downloaded files.
- First, enter md5deep country1.doc. Repeat for country2.doc. (a) What are the lengths of the two hashes? (b) What does the length tell you about the strength of the MD5 hash?
- Now try sha1deep, sha256deep and whirlpooldeep on these two doc files. (c) What are the hashes for each of these files for each of these algorithms? (d) What are their differences?
- Exit all programs. Using Internet Explorer – go to: http://logos.cs.uic.edu/340%20Notes/rsa.html and read the information about the
demonstration. - Chose values 31 for p (Prime 1) and 37 for q (Prime 2), and thus their product will be
- Enter this in ‘n’. Choose 7 for e and enter it into the box. Then click on ‘Generate keys’. This will mean (p-1) (q-1), which comes out at 1080. (e) Explain how e, d are generated.
- Now we have our keys; next scroll down to “RSA Encryption”. Click on the button: “Take public key from above”.
- Encrypt the letter “S” (Encode it as a number and then encrypt). (f) What is the encrypted letter S as a number?
- Encrypt the letter “T”. Scroll down to “RSA Decryption”. Again click on the button: “Take public key from above” and decode the message (g) What is your outcome? (h) Does it match the letter you encoded above in 10 above? If you have an ‘undefined’ error, go back to the top and generate the keys again.
The document file with all 10 exercises have been attached.
Answer preview for Complete the following Information Security Technologies assignment
Access the full answer containing 1970 words by clicking the below purchase button
